Sample DNS Hijack against an unsecured router
As a follow up to the last article about exposed home routers / CPE, here’s a sample, very simple DNS hijack attack using a spare router I have (just in case anyone didn’t believe me).
Given that almost every home router I have ever come across allows the user to set the WAN DNS servers from the admin interface, this is quite easy to do. Now, ideally we would change it on the WAN interface, as it would mean no changes are apparent on the client.
Note: This is my own router, not someone else’s.
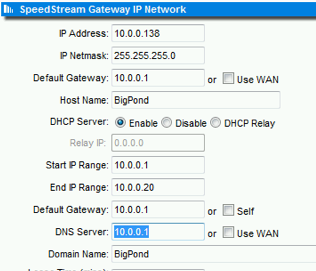
With my test setup though, I’m not using the WAN interface of the router, so I’m going to change DNS in the DHCP settings, which means that clients will lookup addresses directly against the new address
This would allow an attacker to hijack DNS queries and send certain requests (Online banking, Gmail, etc) to their own systems to steal the credentials.
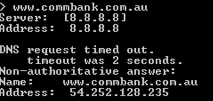
First of all, lets check what the current address returned for www.commbank.com.au is:
Okay, that was using Google’s public DNS system. Now I log into my vulnerable router and change the DNS settings to point to a system of my choosing:
I know what you’re thinking, that looks normal… I am using a DNS server setup on the local test network, but this would work for any server out on the Internet. It’s just more convenient for me to do this on my test network
So now the DNS server has been changed to potentially a nasty address – All clients DNS requests are now answered by our evil DNS server – Which can either forward requests to get the correct address, or respond with an authoritative answer to redirect the browser to our own website whilst retaining that domain name.
I just sent the browser to this site, but it’s not hard for an attacker to imitate a legitimate site in order to harvest credentials.
Of course, in this situation there is no SSL (No green address bar, no little padlock), so you should bail out immediately and not enter your credentials. An attacker could use a faked SSL certificate, but you would be warned by your browser not to continue due to a self-signed cert.
Other hypothetical sneaky attacks could include:
- Injecting malicious content into unencrypted HTTP responses.
- Collect data on browsing habits, usage patterns, etc.
- Use the router as an entry point into your home network.