CryptoWall 3.0: still alive.
Note: This is not yet a full analysis.
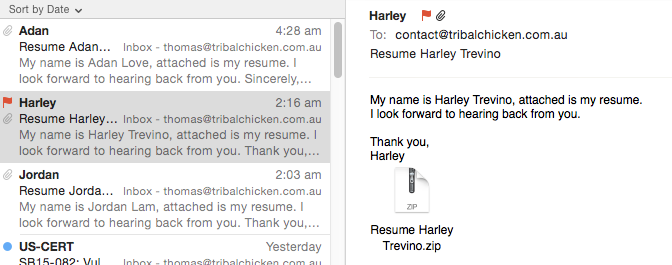
Early this morning I received several phishing emails that look suspiciously like those associated with the delivery of Cryptowall 3.0….
The zip files contain an obfuscated .js file.
Unfortunately I did not get time to take a look until I got home from work. But sure enough, after having a poke around, we have Cryptowall 3.0…
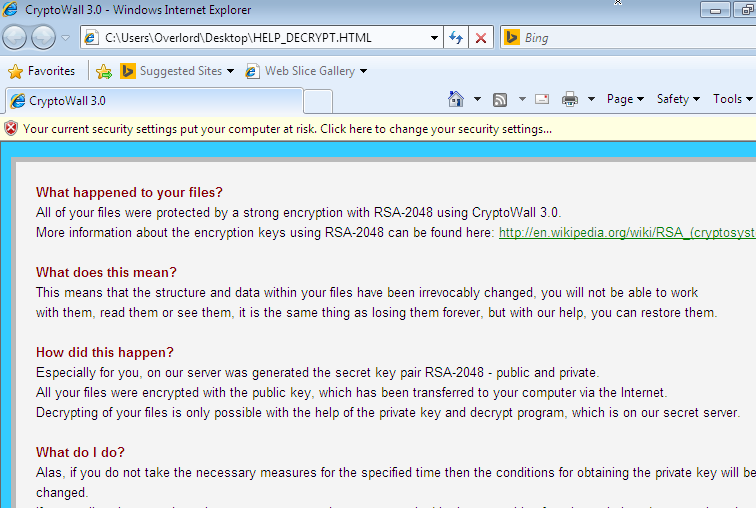
Cryptowall is a clone of CryptoLocker – A Ransomware trojan which, if allowed to infect the host PC, will encrypt files on local and mounted network drives. The decryption key is only stored on the malware’s control servers, rendering your files inaccessible unless you pay the ransom to (hopefully) retrieve the key.
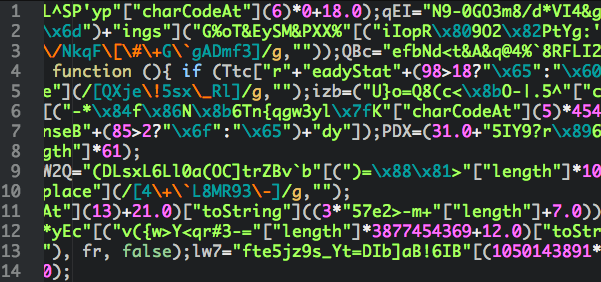
The .js file is lightweight and heavily obfuscated:
The purpose of the .js file is to download two executable files (one.jpg and two.jpg). Don’t be fooled by the name – as previous analysis have noted the files are named thus to evade poorly configured Intrusion Detection Systems.
The two executables (hashes at the bottom of the article) have first been seen by VirusTotal 2 hours before the time of writing.
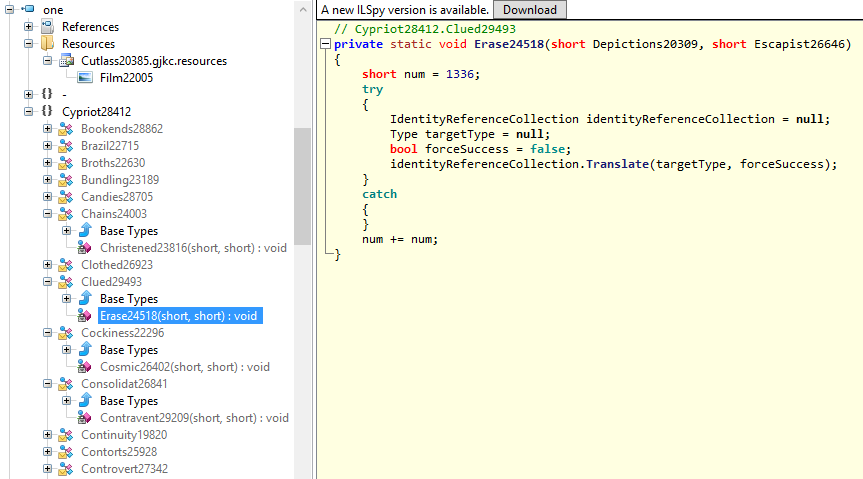
These two executables appear to identify as C# .NET assemblies, and will be happily decompiled by a .NET decompiler:
As you can see there is a heavy level of obfuscation within the decompiled code.
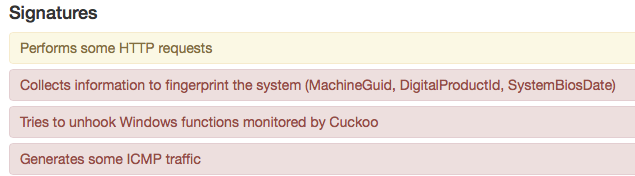
Unfortunately it will refuse to run properly within my Cuckoo instance (Having said that, I did only just reconfigure the VM’s and have not gone to any extra effort to cloak them…. yet) so I was unable to quickly capture any useful traffic.
Further analysis to come soon.
SHA-1 Hashes:
- ZIP Attachment:
e87057ed5583f320138f93c16142fa83751a4182 - .js File:
ff2a4662f85e96e66fbb3310158e9ac7e21cc2bc - one.jpg:
b012adfbb775b9bdcb97f0f6499cef78c1d164eb - two.jpg:
e8507e6247c05a43f003c7564abb3d5abf250f85
For samples or feedback, please contact me.