Crypt0L0cker - TorrentLocker Rebranded
Recently here in Australia there has been some discussion about a Ransomware campaign using Australian Federal Police themed spam emails (The AFP published a press release on the matter in April). The malware shares many characteristics with TorrentLocker and looks to be nearly identical.
This is fairly generic information about this Crypt0L0cker variant, not a full analysis. I’ll update this article if/when I have new information.
So far, from what I have seen, an Encrypting Ransomware variant identifying itself as Crypt0L0cker is being distributed via spam claiming that the victim has obtained a fine for a driving violation, and must click on the link to view the fine.
Here is an example of one of the emails you may receive, annotated to help point out indicators that is a false email:
There are a few indicators pointing to this being a malicious email, however the use of the AFP theme is designed to scare people (so they tend to panic and miss the indicators). It seems to be an effective technique.
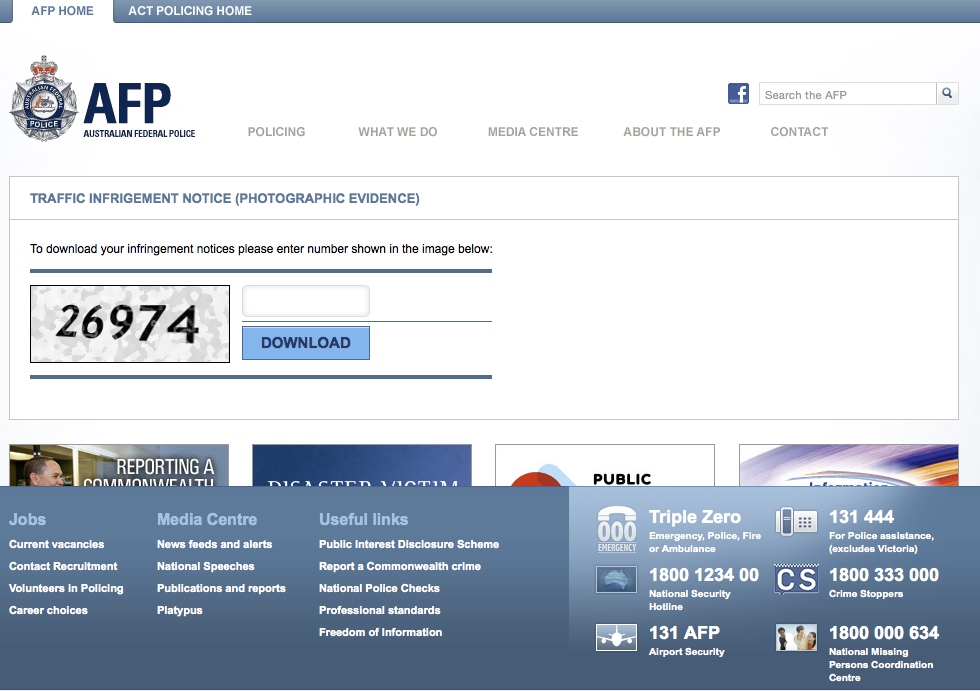
Upon clicking the link a victim will be taken to a replica AFP site (which is very convincing) and asked to enter a CAPTCHA image in order to proceed, presumably a countermeasure against automated URL analysis and to lull the victim into a false sense of security.
Of course, this is Windows malware, so Mobile or Apple users are encouraged to visit the link on their friendly neighbourhood Windows PC (This is an identical message to TorrentLocker):
This webpage does not support mobile/MAC browser. Please use PC browser to view the content.
Upon entering the CAPTCHA the would-be victim is redirected to a file hosted on the file-sharing service *copy.com, *and the file downloaded via their web browser.
The packed executable only gets a VT detection ratio of 7/56, though the unpacked binary (extracted from memory) is identified as a variant of W32/Teerac.A
At this point, in order to be infected you would still need to open the ZIP file and run the malware, which is disguised as a PDF document.
Upon execution, the malware will inject itself into a new instance of explorer.exe.
It will also call *vssadmin.exe *to delete any Volume Shadow Copies you may have (Very common amongst encrypting ransomware) in order to make file recovery difficult.
This sample of Crypt0L0cker performs its Command & Control requests to a single hardcoded domain over an SSL encrypted session. So far my system has been unable to intercept and decode the SSL traffic (it does not appear to be trusting the system certificates and performs some kind of validation) which makes SSL stripping a little more challenging. I’ll come back to that when I have more time.
Normally during this communication a system fingerprint will be sent to the server and in return an encryption key will be returned.
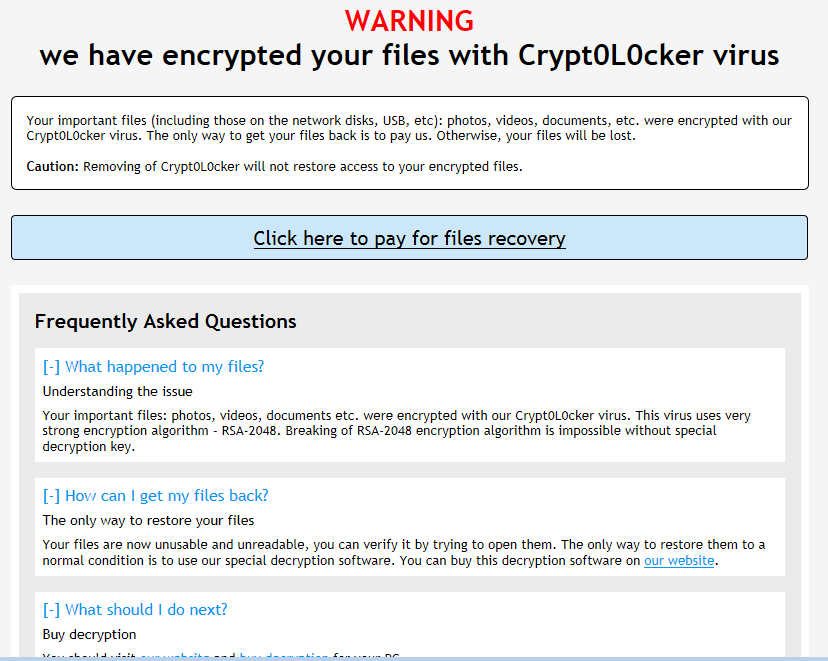
Once the C2 exchange has completed the malware will begin encrypting all files on the system, including those on external disks and network shares. Any file which has an extension that matches Crypt0L0cker’s list will be renamed with a .encrypted file extension and encrypted in-place (This further reduces the chance of file recovery). The Ransom pages are then displayed:
As with TorrentLocker, the link to the payment page is onion-routed via TOR (or a Tor2Web gateway), although the actual server appears to be the same server as as the hardcoded C2 server.
It has striking similarities to the TorrentLocker template:
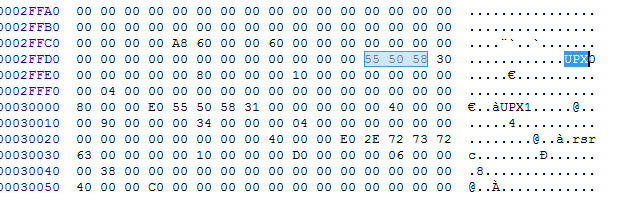
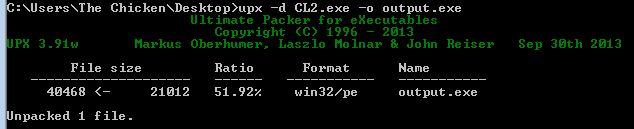
A side note – Interestingly enough the extracted binary appears to contain a UPX packed copy of Win32/Yemrok.A:
I haven’t had much of a look, but from Microsoft’s description perhaps this is used for C2 comms? VirusTotal Link here.
Although I haven’t done a full analysis the observed behaviour of Crypt0L0cker is very *very *similar to TorrentLocker.
Conclusion
This sample appears to be another variant of the TorrentLocker malware, just presenting itself with an ever-so-slightly different name. Crypt0L0cker shares a lot of characteristics with pervious TorrentLocker variants
- Distribution page and ransom page are nearly identical to TorrentLocker campaigns.
- Observed behaviour is similar to TorrentLocker.
- Use of a single hard-coded C2 domain are similar.
- Information-stealing functions are similar.
It would be interesting to compare the two.
If you are infected with encrypting ransomware there is generally no remediation. You will need to wipe your system and restore your files from an offline backup.
References
The ESET paper on Torrent Locker is particularly helpful in drawing comparisons:
http://www.welivesecurity.com/wp-content/uploads/2014/12/torrent_locker.pdf
Also:
http://malware.dontneedcoffee.com/2015/03/cryptofortress-teeraca-aka.html
http://www.microsoft.com/security/portal/threat/Encyclopedia/Entry.aspx?Name=Ransom:HTML/Teerac.A
http://blog.fox-it.com/2014/10/15/torrentlocker-spreading-in-the-netherlands/
Please contact me with any feedback or if you would like a sample.
Speaking of Ransomware, stay tuned for my writeup of the CryptoWall 3.0 + FAREIT Bundle in the next week or two.