A look inside a malicious macro
An interesting sample landed in my samples database the other day. It’s an email with a word document attached. The email, as usual, claims that this company has found discrepancies on some transactions, and needs you to read the document to verify these transactions. [https://tribalchicken.net/content/images/2015/02/Screen-Shot-2015-02-11-at-9.30.19-pm.… continue reading
Location-aware bushfire SMS alerts
I’ve put together a small Python script which can be used to subscribe to a CAP (Common Alerting Protocol) feed, analyse basic information and push it out my SMS Gateway [https://tribalchicken.com.au/?p=307]if the alert fits certain location criteria. [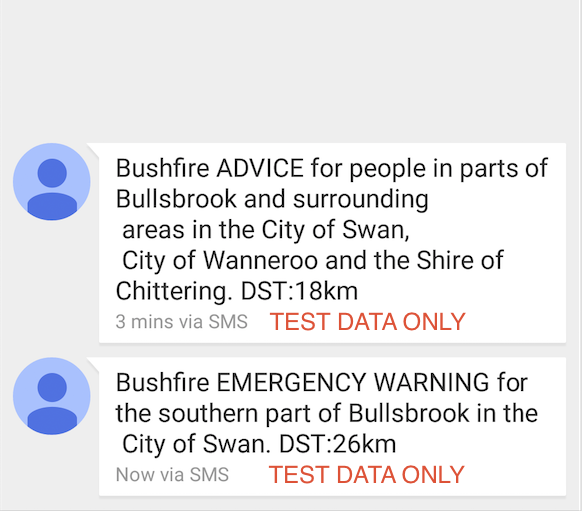](/content/images/2015/… continue reading
Thunderstrike: EFI rootkit for MacBooks
Well this is cool. Trammell Hudson presents his Thunderstrike exploit. > In this presentation we demonstrate Thunderstrike, a vulnerability that allows the installation of persistent firmware modifications into the EFI boot ROM of Apple’s popular MacBooks. The bootkit can be easily installed by an evil-maid via the externally accessible Thunderbolt ports and can survive… continue reading
Code and stuff
Here is some code and bits and pieces of old projects I have floating around and no longer work on. There are two projects here, one is a GSM tracker for the car. The other is a Nerf autonomous sentry gun. These were small hobby projects so a lot of it is unfinished and undocumented.… continue reading
OS X's internal malware protection systems.
For quite some time there has been a common misconception that Mac’s are ‘safer’, or are not susceptible to malware. Unfortunately this is not strictly true. With OS X continuing to gain market share, it will become a more juicy target for cyber criminals. On the plus side though, Apple has included a form… continue reading